What you can do is encrypt a folder that has the files you want to protect. You do this through disk utility. Step by step instructions can be found at the following links: Encrypt files for safety. How to Use Apple’s Built-in Features to Encrypt Files and Folders.
- How To Encrypt Folder Mac
- Mac Folder Encryption App Shortcut
- Mac Folder Encryption App Windows 10
- Mac Folder Encryption App Installer
- Encryption For Mac
By Gina Barrow, Last updated: April 24, 2020
Encryption is the safest and best way to protect data as it encodes a certain file or information in such a way that only authorized users or those with passwords can access. Information including bank details, sensitive personal records should be encrypted to avoid data theft.
Computer operating systems have built-in encryption features but these provide easy to medium form of security and still prone to expert hackers. You need to invest in encryption software if it is a requirement for your type of usage. Here are the top 5 best encryption software for Macin 2020. Check out which one works for your needs.
Part 1. Why Need to Encrypt Mac Files?
All vital files stored inside a computer including Mac need to be encrypted for security purposes. If you happen to hear, watch, and read the news, there are reported cases of stolen identities and bank information due to unsecured files saved inside people’s stolen laptops and computers.
To avoid such hassle, you can rely on encryption software for Mac but the main concern here is what the best software to use is.
Part 2. Apple’s Encryption Software for Mac for free
If you are concerned about data privacy and your Mac contains sensitive information that must be kept personal, then you should use encryption. Apple has its own encryption software that users can utilize for free. There are actually different ways on how to encrypt files on Mac.
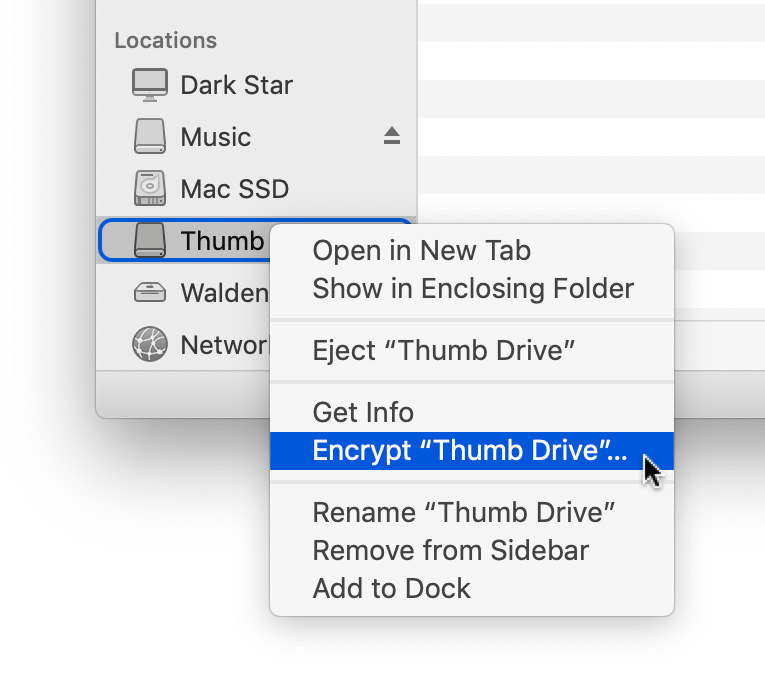
Encryption via Disk Utility
- Use the spotlight search and type in Disk Utility. You can also go to Utilities under Applications.
- Go to File on the topmost tools and hover to New Image then click on Image from Folder
- Select the folder you wish to encrypt from the newly popped-up window
- Rename the file you want to encrypt and go to the bottom part where you can set the encryption settings
- You can choose between the 128 and the 256-bit. (The higher the encryption the better but it takes slower time to complete request)
- Once you have selected your encryption method, you need to provide and verify your password. (Note: Remember your password because it will never grant you access to the given folder until the correct password is supplied). Click Choose.
- For the Image format, you can choose compressed.
- Wait until the encryption is completed.
This type of encryption affects the folder and its file contents so anytime you wish to open the folder and the files inside, you need to provide the password.
- You can now see a new Archive folder on the desktop which was the same file you encrypted
- You can delete the old folder to remove any access to it
People Also ReadHow to Clean up A MacHow Do You Speed Up Your Mac?
Use FileVault
FileVault is full-disk encryption that uses XTS-AES-128 encryption with a 256-bit key to preventing unauthorized access to your personal information on the startup disk. Basically, you won’t be able to go through Mac unless you provide the password.
The FileVault2 is available in OS X Lion and later versions. All you need to take advantage of this feature is to turn on FileVault in your Mac. Here’s how:
- Go to Security & Privacy under System Preferences
- Click the FileVault tab and click on the lock icon
- Enter the administration username and password
- Turn on FileVault
If you are using multiple users on Mac, you can enable each user and type in their assigned password.
Print to PDF
Another file encryption method in Mac is the Print to PDF wherein you can do the security lock on the print window itself after creating or editing certain file/s.
- Go to Print
- Choose PDF
- Click Save as PDF
- Before saving it, go to Security Options
- Check the box for your desired password security measures
- Don’t forget to verify the password and click Save
Part 3. The Best Encryption Software for Mac in 2020
In the sea of many software and applications, there seems to be plenty of programs dedicated to single-use or single-function. They are good because they focus on one solution, however, they also cost more expensive.
If you browse thoroughly, you will discover that there are a few applications that offer sets of operations and toolkits specially designed for Mac. FoneDog PowerMyMac - Cleaner provides comprehensive modules dedicated to Mac OS. It has three powerful modules: Toolkit, Status, and Cleaner.
Inside FoneDogPowerMyMac-Cleaner Toolkit, there is a robust function called Hide and Encrypt Files. This feature allows you to create a password-protected folder and store sensitive files in it by drag and drop. It lets you turn on and off in case you may not use the feature.
- User-friendly
- Free download version
- Auto-lock setup
- Uses the safest encryption system
How cool is that? This program has made an easier way to protect you from possible data theft.
Part 4. Other Mac Encryption Tools
Apart from FoneDog PowerMyMac-Cleaner, there is other top performing software that also provides convenience and security.
Hider 2
Hider2 has the ability to hide and encrypt data on your Mac securely including notes, documents, photos, etc. One of its positive scores is the user-friendly interface which suits beginner to average users.
- Provides auto-lock feature when the user is inactive or idled
- Uses AES-256 encryption for the safest system
Cisdem AppCrypt
Cisdem AppCrypt offers both website and app encryption system that locks you apps and accessed websites with passwords. It creates a blacklist for suspicious access and whitelist for trusted users. However, it does not have the file encryption ability that sets passwords for the desired file and folders.
- Keeps a list of login attempts to let you know who opens your apps
- User-friendly
GNU Privacy Guard
GNU Privacy Guard is hybrid Mac encryption software that uses a combination of standard symmetric-key cryptography and public-key cryptography. It mainly features a versatile key management system to protect your personal privacy and the privacy of the people you are communicating with.
- Versatile (has Windows and Mac versions)
- Free Software
However, since it provides you with a private key for safekeeping, you might end up having a hard time figuring out how to decode it once the keys are lost.
Concealer
Concealer is another trusted name in terms of hiding files and encryption. It provides an automatic password assistant that generates “strong” passwords. One of its main advantages is providing and organizing folders by having default templates for various accounts such as bank accounts, email, software registration, and more.
- Customizable auto-lock system
- Easy to use with drag and drop features
- Uses the master password and assigns separate or individual passwords to each file inside
Part 5. Factors to Consider when Choosing the Best Encryption Software for Mac
I know you may have gotten confused on which program to use or will work best for you after reading through the different software you can choose from. There is plenty of encryption software for Mac; however, bear in mind that you need to consider quality and multi-function when it comes to having a “good buy”.
How To Encrypt Folder Mac
You need a program that provides an all-in-one solution that you can rely on when things go rough on your device. I recommend using FoneDog PowerMyMac for the following factors:
- Security– It the important concern above all. You have to be keen about how these programs work to secure your files and your Mac overall.
- Encryption– Based on the above-mentioned encryption data, there are different types of password-protection format. Choose the one that provides the safest and considers your files their topmost priority.
- Encryption Speed- Consider a program that can encrypt even your large files at the shortest period of time. We know that large files take a while to be fully encrypted so you need software that can minimize the time constraints.
- Software License- Although free programs are good such as the GNU Privacy Guard, an open source software, you need to consider that free software is not entirely best for your needs since everyone can download it. The same thing goes for paid programs; you have to be extra cautious on how much it costs and its corresponding features. To be sure, you can take advantage of their free-trial versions first so you can determine if it works for you or not.
Part 6. Conclusions
We care so much about data privacy and we understand how crucial it is to be well-protected. You cannot simply store important files in your Mac especially when you have multiple users or you plan to sell it later on.
We know how much you want to protect your files from prying eyes and suspicious people that is why we have compiled and researched the different programs that can help you secure them. The encryption software for Mac we listed has their own Pros and Cons where you can assess according to their features.
Simply choose a program that will password-protect your files, optimize your system, and provide you with complete troubleshooting toolkit. Do you have any other concerns regarding encryption software for Mac? Please write your concerns in the comments below!
In cryptography, a message authentication code (MAC), sometimes known as a tag, is a short piece of information used to authenticate a message—in other words, to confirm that the message came from the stated sender (its authenticity) and has not been changed. The MAC value protects a message's data integrity, as well as its authenticity, by allowing verifiers (who also possess the secret key) to detect any changes to the message content.
Definitions[edit]

Informally, a message authentication code system consists of three algorithms:
- A key generation algorithm selects a key from the key space uniformly at random.
- A signing algorithm efficiently returns a tag given the key and the message.
- A verifying algorithm efficiently verifies the authenticity of the message given the key and the tag. That is, return accepted when the message and tag are not tampered with or forged, and otherwise return rejected.
For a secure unforgeable message authentication code, it should be computationally infeasible to compute a valid tag of the given message without knowledge of the key, even if for the worst case, we assume the adversary can forge the tag of any message except the given one.[1]
Formally, a message authentication code (MAC) system is a triple of efficient[2] algorithms (G, S, V) satisfying:
- G (key-generator) gives the key k on input 1n, where n is the security parameter.
- S (signing) outputs a tag t on the key k and the input string x.
- V (verifying) outputs accepted or rejected on inputs: the key k, the string x and the tag t.
S and V must satisfy the following:
- Pr [ k ← G(1n), V( k, x, S(k, x) ) = accepted ] = 1.[3]
A MAC is unforgeable if for every efficient adversary A
- Pr [ k ← G(1n), (x, t) ← AS(k, · )(1n), x ∉ Query(AS(k, · ), 1n), V(k, x, t) = accepted] < negl(n),
where AS(k, · ) denotes that A has access to the oracle S(k, · ), and Query(AS(k, · ), 1n) denotes the set of the queries on S made by A, which knows n. Clearly we require that any adversary cannot directly query the string x on S, since otherwise a valid tag can be easily obtained by that adversary.[4]
Security[edit]
While MAC functions are similar to cryptographic hash functions, they possess different security requirements. To be considered secure, a MAC function must resist existential forgery under chosen-plaintext attacks. This means that even if an attacker has access to an oracle which possesses the secret key and generates MACs for messages of the attacker's choosing, the attacker cannot guess the MAC for other messages (which were not used to query the oracle) without performing infeasible amounts of computation.
MACs differ from digital signatures as MAC values are both generated and verified using the same secret key. This implies that the sender and receiver of a message must agree on the same key before initiating communications, as is the case with symmetric encryption. For the same reason, MACs do not provide the property of non-repudiation offered by signatures specifically in the case of a network-wide shared secret key: any user who can verify a MAC is also capable of generating MACs for other messages. In contrast, a digital signature is generated using the private key of a key pair, which is public-key cryptography[2]. Since this private key is only accessible to its holder, a digital signature proves that a document was signed by none other than that holder. Thus, digital signatures do offer non-repudiation. However, non-repudiation can be provided by systems that securely bind key usage information to the MAC key; the same key is in the possession of two people, but one has a copy of the key that can be used for MAC generation while the other has a copy of the key in a hardware security module that only permits MAC verification. This is commonly done in the finance industry.[citation needed]
Message integrity codes[edit]
The term message integrity code (MIC) is frequently substituted for the term MAC, especially in communications,[5] to distinguish it from the use of MAC meaning MAC address (for media access control address). However, some authors[6] use MIC to refer to a message digest, which is different from a MAC – a message digest does not use secret keys. This lack of security means that any message digest intended for use gauging message integrity should be encrypted or otherwise be protected against tampering. Message digest algorithms are created such that a given message will always produce the same message digest assuming the same algorithm is used to generate both. Conversely, MAC algorithms are designed to produce matching MACs only if the same message, secret key and initialization vector are input to the same algorithm. Message digests do not use secret keys and, when taken on their own, are therefore a much less reliable gauge of message integrity than MACs. Because MACs use secret keys, they do not necessarily need to be encrypted to provide the same level of assurance.
RFC 4949 recommends avoiding the term 'message integrity code' (MIC), and instead using 'checksum', 'error detection code', 'hash', 'keyed hash', 'message authentication code', or 'protected checksum'.
Implementation[edit]
MAC algorithms can be constructed from other cryptographic primitives, like cryptographic hash functions (as in the case of HMAC) or from block cipher algorithms (OMAC, CCM, GCM, and PMAC). However many of the fastest MAC algorithms like UMAC-VMAC and Poly1305-AES are constructed based on universal hashing.[7]
Intrinsically keyed hash algorithms such as SipHash are also by definition MACs; they can be even faster than universal-hashing based MACs.[8]
Additionally, the MAC algorithm can deliberately combine two or more cryptographic primitives, so as to maintain protection even if one of them is later found to be vulnerable. For instance, in Transport Layer Security (TLS), the input data is split in halves that are each processed with a different hashing primitive (SHA-1 and SHA-2) then XORed together to output the MAC.
Standards[edit]
Various standards exist that define MAC algorithms. These include:
- FIPS PUB 113 Computer Data Authentication,[9] withdrawn in 2002,[10] defines an algorithm based on DES.
- FIPS PUB 198-1 The Keyed-Hash Message Authentication Code (HMAC)[11]
- ISO/IEC 9797-1Mechanisms using a block cipher[12]
- ISO/IEC 9797-2 Mechanisms using a dedicated hash-function[13]
- ISO/IEC 9797-3 Mechanisms using a universal hash-function[14]
- ISO/IEC 29192-6 Lightweight cryptography - Message authentication codes[15]
ISO/IEC 9797-1 and -2 define generic models and algorithms that can be used with any block cipher or hash function, and a variety of different parameters. These models and parameters allow more specific algorithms to be defined by nominating the parameters. For example, the FIPS PUB 113 algorithm is functionally equivalent to ISO/IEC 9797-1 MAC algorithm 1 with padding method 1 and a block cipher algorithm of DES.
An example of MAC use[edit]
[16]In this example, the sender of a message runs it through a MAC algorithm to produce a MAC data tag. The message and the MAC tag are then sent to the receiver. The receiver in turn runs the message portion of the transmission through the same MAC algorithm using the same key, producing a second MAC data tag. The receiver then compares the first MAC tag received in the transmission to the second generated MAC tag. If they are identical, the receiver can safely assume that the message was not altered or tampered with during transmission (data integrity).
Mac Folder Encryption App Shortcut
However, to allow the receiver to be able to detect replay attacks, the message itself must contain data that assures that this same message can only be sent once (e.g. time stamp, sequence number or use of a one-time MAC). Otherwise an attacker could – without even understanding its content – record this message and play it back at a later time, producing the same result as the original sender.
One-time MAC[edit]
Mac Folder Encryption App Windows 10
Universal hashing and in particular pairwise independent hash functions provide a secure message authentication code as long as the key is used at most once. This can be seen as the one-time pad for authentication.[17]
The simplest such pairwise independent hash function is defined by the random key key = (a,b), and the MAC tag for a message m is computed as tag = (am + b) mod p, where p is prime.
More generally, k-independent hashing functions provide a secure message authentication code as long as the key is used less than k times for k-ways independent hashing functions.
See also[edit]
- Hash-based message authentication code (HMAC)
Notes[edit]
- ^The strongest adversary is assumed to have access to the signing algorithm without knowing the key. However, her final forged message must be different from any message she chose to query the signing algorithm before. See Pass's discussions before def 134.2.
- ^ abTheoretically, an efficient algorithm runs within probabilistic polynomial time.
- ^Pass, def 134.1
- ^Pass, def 134.2
- ^IEEE 802.11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications(PDF). (2007 revision). IEEE-SA. 12 June 2007. doi:10.1109/IEEESTD.2007.373646. ISBN978-0-7381-5656-9.
- ^Fred B Schneider, Hashes and Message Digests, Cornell University
- ^'VMAC: Message Authentication Code using Universal Hashing'. CFRG Working Group. CFRG Working Group. Retrieved 16 March 2010.
- ^Jean-Philippe Aumasson & Daniel J. Bernstein (2012-09-18). 'SipHash: a fast short-input PRF'(PDF).
- ^'FIPS PUB 113 Computer Data Authentication'. Archived from the original on 2011-09-27. Retrieved 2010-10-10.
- ^'Federal Information Processing Standards Publications, Withdrawn FIPS Listed by Number'. Archived from the original on 2010-08-01. Retrieved 2010-10-10.
- ^The Keyed-Hash Message Authentication Code (HMAC)
- ^ISO/IEC 9797-1 Information technology — Security techniques — Message Authentication Codes (MACs) — Part 1: Mechanisms using a block cipher
- ^ISO/IEC 9797-2 Information technology — Security techniques — Message Authentication Codes (MACs) — Part 2: Mechanisms using a dedicated hash-function
- ^ISO/IEC 9797-3 Information technology — Security techniques — Message Authentication Codes (MACs) — Part 3: Mechanisms using a universal hash-function
- ^ISO/IEC 29192-6 Information technology — Lightweight cryptography — Part 6: Message authentication codes (MACs)
- ^'Mac Security Overview', Mac® Security Bible, Wiley Publishing, Inc., 2011-11-01, pp. 1–26, doi:10.1002/9781118257739.ch1, ISBN9781118257739
- ^Simmons, Gustavus (1985). 'Authentication theory/coding theory'. Advances in Cryptology: Proceedings of CRYPTO 84. Berlin: Springer. pp. 411–431. ISBN00000000 Check
|isbn=value: length (help).
References[edit]
- Goldreich, Oded (2001), Foundations of cryptography I: Basic Tools, Cambridge: Cambridge University Press, ISBN978-0-511-54689-1
- Goldreich, Oded (2004), Foundations of cryptography II: Basic Applications (1. publ. ed.), Cambridge [u.a.]: Cambridge Univ. Press, ISBN978-0-521-83084-3
- Pass, Rafael, A Course in Cryptography(PDF), retrieved 31 December 2015[1]
External links[edit]
Mac Folder Encryption App Installer
- ^11-12-20C8